thick client application security testing pdf|thick client pentest checklist : bespoke Thick client applications pose unique security challenges that require specialized knowledge and techniques to assess effectively. This repository serves as a guide for . Euromilhoes. Resultados anteriores. Lista de todas as chaves já saídas. Calendario. Toggle navigation Últimos resultados. Sorteios Euromilhões. . Ultimos resultados; Inicio; Jackpot euromilhoes; Horário sorteios; Sorteios anteriores. Euromilhões terça 27 de fevereiro 2024;
{plog:ftitle_list}
Resultado da NUA BIA: Crafting Plant-Based Food Classics in Dublin, Ireland. Experience the best of Irish plant-based cuisine with NUA BIA. We're a Dublin-based .
Thick client applications pose unique security challenges that require specialized knowledge and techniques to assess effectively. This repository serves as a guide for .The OWASP Thick Client Project is a standard awareness document for .Test GUI Content. Look for sensitive information. Test For GUI Logic. Try for .
In this post, I’d like to share my methodology to test thick clients to find security issues. A thick client is a type of application where the bulk of .Neelay S Shah March 24, 2010. Types of thick client applications. Tools and techniques for security testing. Questions. For today’s presentation. Bypass client side validation checks. .This project provides a comprehensive framework for designing, building, and testing technical application security controls, addressing architectural concerns, secure development .The TASVS Project fills the gap between the OWASP Application Security Verification Standard (ASVS) for web applications and the Mobile Application Security Verification Standard (MASVS). While the MASVS can be applied to thick client testing, it is not an ideal fit. The TASVS Project seeks to create a more suitable standard for these scenarios.
Microsoft Outlook, Yahoo Messenger, and Skype are some thick client application examples. How to test thick client applications? 👨💻. Thick Client Pentest is complicated as compared to /API Pentest in my opinion. .
thick client testing tool
Leadership | Meet the team guiding Black Duck's vision and strategy.; Newsroom | Latest news, press releases, and media coverage about Black Duck.; Blog | Insights, updates, and expert opinions on application security.; Partners | Information on Black Duck's partnerships and collaboration opportunities.; Careers | Explore job opportunities and career paths at Black Duck.TRAFFIC TESTING. Test For Traffic. Analyze the flow of network traffic; Try to find sensitive data in transit; Tools Used. Echo Mirage; MITM Relay; Burp Suite; COMMON VULNERABILITIES TESTING. Test For Common Vulnerabilities. Try to decompile the application; Try for reverse engineering; Try to test with OWASP Top 10; Try to test with OWASP .Enhanced Integration Security: Thick Client Penetration Testing at Securityium significantly enhances integration security by accurately examining how thick client applications interact with other systems and services. Our Thick Client Pentesting identifies vulnerabilities in integration points, such as insecure communication channels and . Thick client application security testing involves comprehensively evaluating vulnerabilities, authentication mechanisms, data encryption, security misconfigurations, and network communication .
Information gathering is a critical initial phase in thick client application penetration testing, focused on collecting detailed data about the application’s architecture, components, and interactions with servers. . Effective information gathering lays the foundation for a thorough security assessment, enabling testers to identify and .
thick client pentest checklist
Thick client applications are unique and testing thick clients requires patience and a methodical approach. A simple automat- . ence in network & web application vulnerability assessment and penetration testing, thick client security, database security, mobile application security, SAP application penetration testing, source code audit, .The Thick Client Application Security Expert (TCSE) is an online training program that provides all the high-level skills required for thick client application security auditing and penetration testing. TCSE training starts with a risk-based analysis of both your thick client software and the server-side APIs.
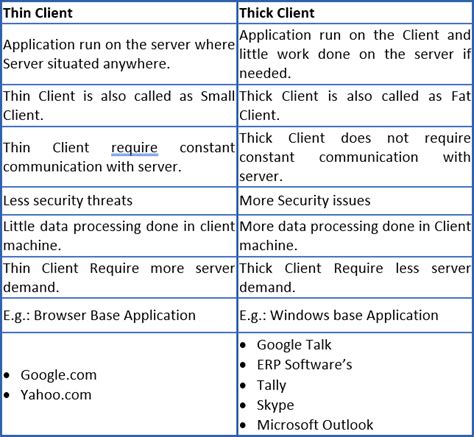
Thick client applications, called desktop applications, are full-featured computers that are connected to a network. Unlike thin clients, which lack hard drives and other features, thick clients are functional whether they are connected to a network or not.
Security. 2-Tier: More vulnerable as the client has direct access to the database.; 3-Tier: Improved security as the application server enforces access control and business rules.; Complexity. 2-Tier: Simpler architecture with fewer components, but direct exposure of the database to the client.; 3-Tier: More complex architecture with an additional layer, providing . Thick Client Penetration Testing Modern Approaches and Techniques.pdf - Download as a PDF or view online for free. . such as malware, phishing, and hacking. We have expertise of conducting Thick Client Application Security Testing on client-server applications adopting proven methods and technology. Get in touch with us for more insights .
Thick client applications can operate without a network connection. To test these applications, you have to understand the entry points for user inputs, application architecture, technologies being used, any propriety protocols, programming languages, and frameworks being used in building it. Read on the blog to know Types of Architecture in Thick . PTES (Penetration Testing Execution Standard), OWASP Testing Guide: OWASP Top 10 and CWE Top 25: Mobile application: PTES (Penetration Testing Execution Standard), OWASP Mobile Security Testing Guide: OWASP Mobile Top 10: Desktop or thick-client applications: PTES (Penetration Testing Execution Standard), OWASP recommended . Thick client penetration testing focuses on identifying vulnerabilities within client-server applications where the client-side application (thick client) performs significant processing.
Digital Thickness Meter tv shopping
Attack surface visibility Improve security posture, prioritize manual testing, free up time. CI-driven scanning More proactive security - find and fix vulnerabilities earlier. Application security testing See how our software enables the world .It represents a broad consensus about the most critical security risks to Desktop applications. Globally recognized by developers as the first step towards more secure coding. Companies should adopt this document and start the process of ensuring that their desktop applications / thick-clients minimize these risks.
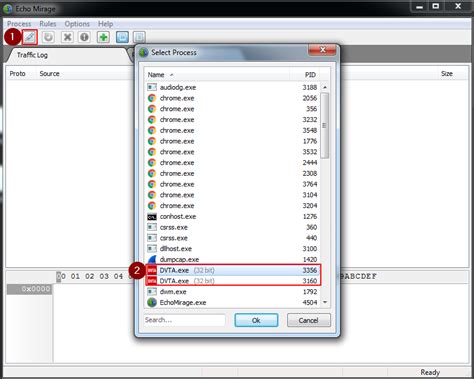
Welcome to the part 7 of Practical Thick Client Application Penetration Testing using Damn Vulnerable Thick Client App (DVTA). In the previous article, we have discussed how to perform .NET application patching using ildasm and ilasm utilities to modify the functionality of a .NET assembly. In this article, we will discuss DLL Hijacking in .Detect security weaknesses that attackers could exploit, ensuring your application is protected from potential threats. Gain insight into how vulnerabilities can be leveraged to gain unauthorized access or escalate privileges, helping to secure your application against advanced attacks. Thick client application security assessment - Download as a PDF or view online for free . PDF • 7 likes • 10,436 views. Sanjay Kumar (Seeking options outside India) Follow. Introduction Difference between Thin & Thick client Approach of security testing Vulnerabilities applicable to thick client General recommendations Read less.
Their extensive use across organizations, often involving critical and sensitive data processing, presents significant security challenges. Thick Client penetration testing is an ethical hacking security assessment carried out to uncover vulnerabilities in the thick client software application, network traffic, and backend interface and .Thick Client Penetration Testing (a.k.a. Thick Client Pentest, Thick Client VAPT, Thick Client Pen Testing) identifies exploitable vulnerabilities on both the local and server-side. The attack surface is larger and requires a different approach from web application penetration testing. If a thick client is built on a three-tier architecture, the network portion of the test will essentially be the same as testing a web application. First order of business is proxying the traffic. In the proxy tab of Burp, set up a listener on 127.0.0.1 and a port of choice. Learn all types of security testing like a black box, white box, and grey-box testing of the thick client application. learn thick client testing with us
Digital Plastic and Rubber Thickness Meter tv shopping
How to identify and exploit common security issues in 2-tier applications. Learn multiple ways to intercept TCP traffic coming from thick client apps. Get real world thick client application penetration testing experience. Learn how to use several .OWASP ZAP, on the other hand, focuses on web application security and provides a comprehensive set of tools for testing thick client applications. Its automated scanning capabilities help identify common vulnerabilities, such as cross-site scripting (XSS) and SQL injection, in both the client-side and server-side components of the application.Thick client penetration testing is an essential component of your overall application security strategy, more particularly for mission-critical apps, as it helps you identify & fix vulnerabilities to ensure your end users have a secure environment to .
thick client penetration testing tools
WEB30 de nov. de 2022 · Após a “brochada nas urnas” (Kid perdeu as eleições para o cargo de deputado federal por São Paulo), ele pretende manter o contato íntimo com os fãs por meio da internet. Kid Bengala. Kid .
thick client application security testing pdf|thick client pentest checklist